What is Okta FastPass and how to set it up
Identity Engine allows customers to further enhance their users passwordless experience, and with Okta Fastpass users can access their apps and resources quick and securely without the need of any additional device. Read more about what it is and how to set it up.

Andreas Faltin
20. June 2022
Okta has established itself as the independent cloud platform for Identity and Access Management. Regularly on top of the Gartner Magic Quadrant for IAM and constantly improving the product. Like all software products, though, there are sometimes structural changes required that cannot be just removed or modified without turning the bigger wheel. This is what the Identity Engine is about. It's not a new product or a different kind of use case, it’s the known Okta platform reengineered.
→ Read an introduction to the Okta Identity Engine
New customers since November 2021 are automatically on Identity Engine. Existing customers will be migrated during 2022.
What is Okta FastPass?
Okta FastPass allows users to sign on to their Okta resources, like Okta Dashboard and all applications, fast and securely via a locally installed Okta Verify on their device.
Users register the device once with their first login to Okta on their device, as well as by using a secure and multifactored authentication, such as Okta Verify on their phone. Once configured, the users can sign in passwordless only using the device they try to use.
True passwordless on each device with Okta FastPass
Administrators can manage Okta FastPass through the Global Session Policy and either integrate Okta FastPass into the ordinary sign on flow or enable the “Okta FastPass” button on the sign in prompt, which allows users to not even provide a username for sign on.
Okta FastPass can be used on Windows, MacOS, iOS and Android devices. Linux devices will be supported soon.
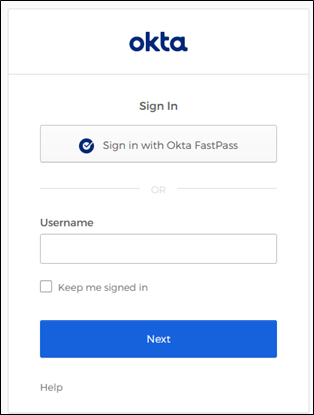 Sign in widget with FastPass button. Not required for FastPass, although recommended
Sign in widget with FastPass button. Not required for FastPass, although recommended
How to setup FastPass
1. Setup Global Session Policy
To configure Okta FastPass you either need to create a new or edit the default Global Session policy (which previously was the “Sign On policy” in Classic Engine tenants).*
The settings required for FastPass is primary factors. It is set to “Password / IDP / any factor allowed by app sign on rules”. If you want to enforce an additional factor you can enable “Require secondary factor”, which then enforces the use of an additional factor with the local Okta Verify, for example, biometrics. Keep in mind not all devices support biometrics and might be blocked from using Okta FastPass. You can alternatively define app-level policies that enforce additional factors to Okta Verify/FastPass.
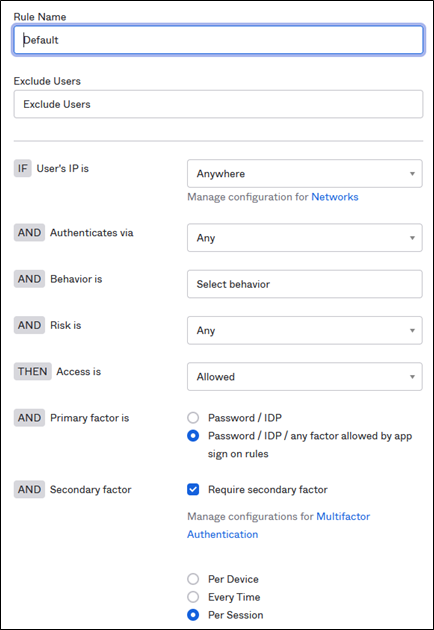 Global Session policy ready for FastPass
Global Session policy ready for FastPass
* Attention: Changing the Global Session policy will have an effect on all sign ins. Make sure you have strong app-level policies in place to maintain your security policies for sign in, like multifactor requirements.
2. Enable FastPass
Since Okta FastPass relies on Okta Verify it is configured and enabled in the Okta Verify authenticator settings under Security → Authenticators → Okta Verify → Actions → Edit.
Here you can configure “Okta Verify (All plattforms)” and then select the option if you want to include the Okta FastPass button on the sign in page:
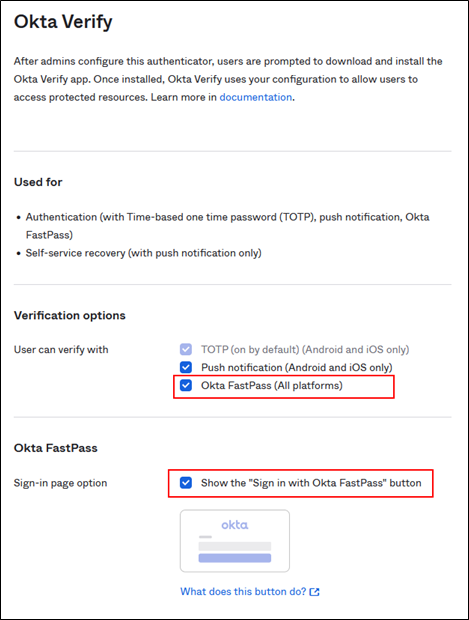 Okta Verify configured for FastPass
Okta Verify configured for FastPass
That’s it, now you have configured Okta FastPass!
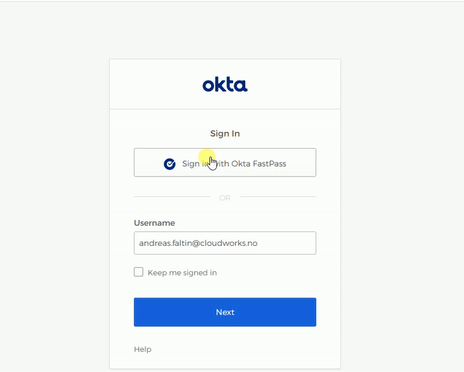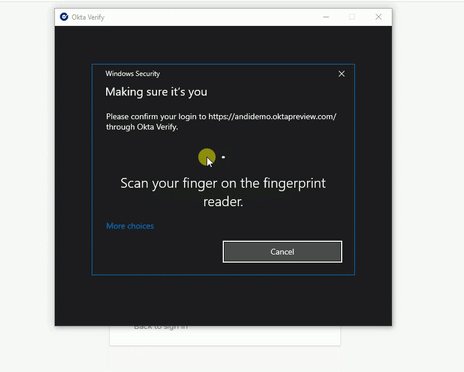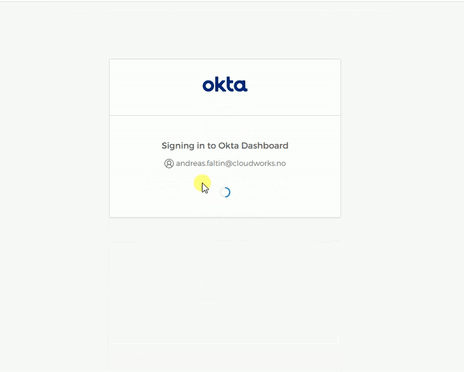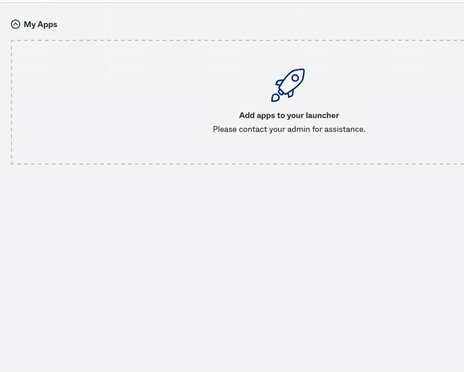
Sign in on a Windows PC with FastPass and biometrics
Use FastPass for device context
FastPass is not only great for your users as it provides them with a secure and easy passwordless login. It can also help you maintain security standards by using the local Okta Verify to determine if a user is coming from a managed device or not. Find out in the next article of the series how device context 2.0 works in Okta Identity Engine. Coming soon!





.png?width=720&name=Okta%20Workflows%20Part%203%20(1).png)




