How FastPass and Devices help you maintain security standards in Okta
In addition to the new key feature FastPass provides a secure and easy passwordless login, it can also help you maintain security standards by using the local Okta Verify to determine if a user is coming from a managed device or not. Find out more about Okta Devices.

Andreas Faltin
30. June 2022
Okta has established itself as the independent cloud platform for Identity and Access Management. Regularly on top of the Gartner Magic Quadrant for IAM and constantly improving the product. Like all software products, though, there are sometimes structural changes required that cannot be just removed or modified without turning the bigger wheel. This is what the Identity Engine is about. It's not a new product or a different kind of use case, it’s the known Okta platform reengineered.
→ Read an introduction to the Okta Identity Engine
New customers since November 2021 are automatically on Identity Engine. Existing customers will be migrated during 2022.
Overview
With Identity Engine Okta is now able to monitor and remember user devices with local installations of Okta Verify on them. The first part of that section, FastPass, we’ve already covered in the previous article. Although it is beneficial to use FastPass for the full functionality set, it is not a requirement for Okta Devices.
Before we go into the technical details a few misconceptions on what Okta Devices is not:
- It is NOT a mobile device management solution, although an MDM can be connected and information from there can be used.
- It does NOT provide a method to pre-enter all your companies’ devices before users have connected with them.
- It does NOT hold all devices that users connect from. For example, if a user connects through a browser on a public PC but uses his/hers Okta Verify on the smartphone for authentication, it is the smartphone that’ll show in the devices, not the computer the browser runs on. You can, however, configure a policy that allows certain apps only on managed, trusted devices with Okta Verify on them.
Managing devices
Under Directory → Devices you can now see all the users' devices with Okta Verify on them. On this page you can search for certain platforms or statuses. To search for a user's devices you can go to the user, there you’ll find a “Devices” tab on their profile.
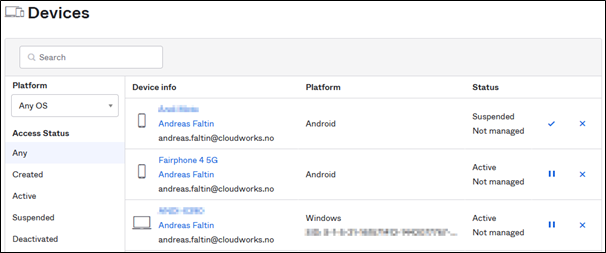 Devices overview
Devices overview
Suspending devices
Existing devices can be administrated by either suspending or deactivating them. Suspending means that all sessions continue to work (except the ones on that device) and the user cannot use this device anymore to establish a new session. Suspended devices can be unsuspended any time without additional efforts required by the user.
Deactivating devices
Deactivating a device means that all active sessions on the device as well as non-Okta Verify sessions will be terminated. If the device gets reactivated the user needs to re-register the device.
During both suspension or deactivation, the user cannot use the device for Okta Verify Authentication (although using the device with password and another factor – if allowed by the sign in policies – will still work) nor enroll a new account in Okta Verify on this device.
Device Management status
Devices can be seen as “managed” or “not managed”. By standard all devices are “not managed”. To get them into a managed state in Okta you need to connect your MDM solution with Okta.
Okta can only determine the device management status if Okta Verify is installed on that device. Okta uses client certificates (Desktop Devices, Windows & macOS) or a management hint/shared secret (mobile devices, iOS & Android) to determine if a device is managed or not.
Configure desktop devices
To configure desktop devices, you can either use Okta’s own certificate authority or your personal CA. The protocol used for enrolling the certificate on the devices is SCEP and the enrollment needs to be configured in your device management solution, like Jamf Pro, VMWare Workspace One or Microsoft Intune /MEM. These are the currently officially supported platforms, although other will work as well.
Configure mobile devices
To configure mobile devices, you can retrieve the secret key from Okta under Security → Device Integrations and need to add the key to your mobile device management to be enrolled to the devices. The MDM can then deploy Okta Verify with the managed app configuration and the secret key.
Use Device Management status
The device management status can then be used in any authentication policy to enforce security standards based on whether the device is managed or not:
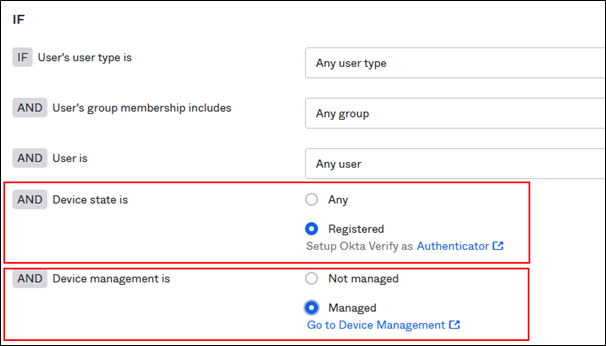 Authentication Policy - Device state & Management
Authentication Policy - Device state & Management
For example, you can enforce an additional multifactor on non-managed devices, while allowing users on managed devices to go through without. Or denying access to certain applications for non-managed devices completely.
Additional options
Integrate your EDR solution
Okta can also integrate with your endpoint detection and response (EDR) solution. When connecting via Okta verify Okta probes the device for context to make the decision for access, for example the management status mentioned previously. Okta can also collect additional signals from the EDR client running on the same device. The currently supported solutions are Crowdstrike and Microsoft Windows Security Center. Support for additional vendors is planned in the future.
Expression language for devices
The powerful Okta Expression language has now been enhanced and can be used in Authentication Policies to further determine the context for authentication:
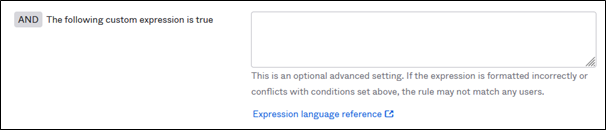 Use Okta Expression language in Authentication Policies
Use Okta Expression language in Authentication Policies
https://developer.okta.com/docs/reference/okta-expression-language-in-identity-engine/





.png?width=720&name=Okta%20Workflows%20Part%203%20(1).png)




